As you know by reading our articles, we emphasize privacy a lot. We believe it is very important, so sometimes, that means keeping certain apps away from curious eyes. Hiding apps on your iPhone is straightforward, whether you’re aiming to declutter your iPhone’s home screen or ensure your privacy. Let’s walk through the steps together.

Woman on an iPhone (Kurt “CyberGuy” Knutsson)
How to hide a single app on an iPhone
First, let us address how to make a single app vanish from your home screen:
- Navigate to the screen with the app you want to hide and long-press the app
- Tap Remove App
- Tap Remove from Home Screen
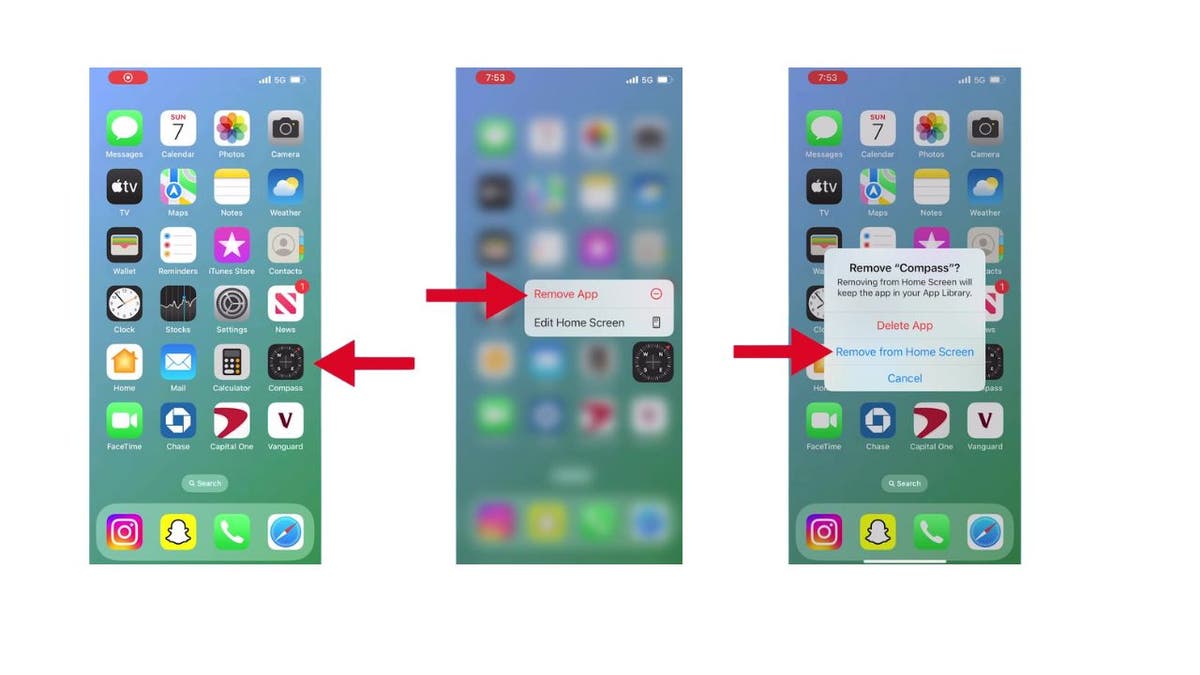
Steps to hide a single app on an iPhone (Kurt “CyberGuy” Knutsson)
The app is now hidden from your home screen but remains accessible through the search function and in your App Library. To access the App Library on your iPhone:
- Go to your home screen.
- Swipe left past all of your home screen pages.
- You’ll see the App Library as the last screen, which organizes your apps into categories.
MORE: BEST ACCESSORIES FOR YOUR PHONE
How to hide a whole page of apps
If you’re looking to hide an entire page of apps, here’s how:
- Long press on an empty area of the home screen
- Tap the dots at the bottom of the home screen
- Tap the check mark under the page you want to remove.
- Next, tap Done
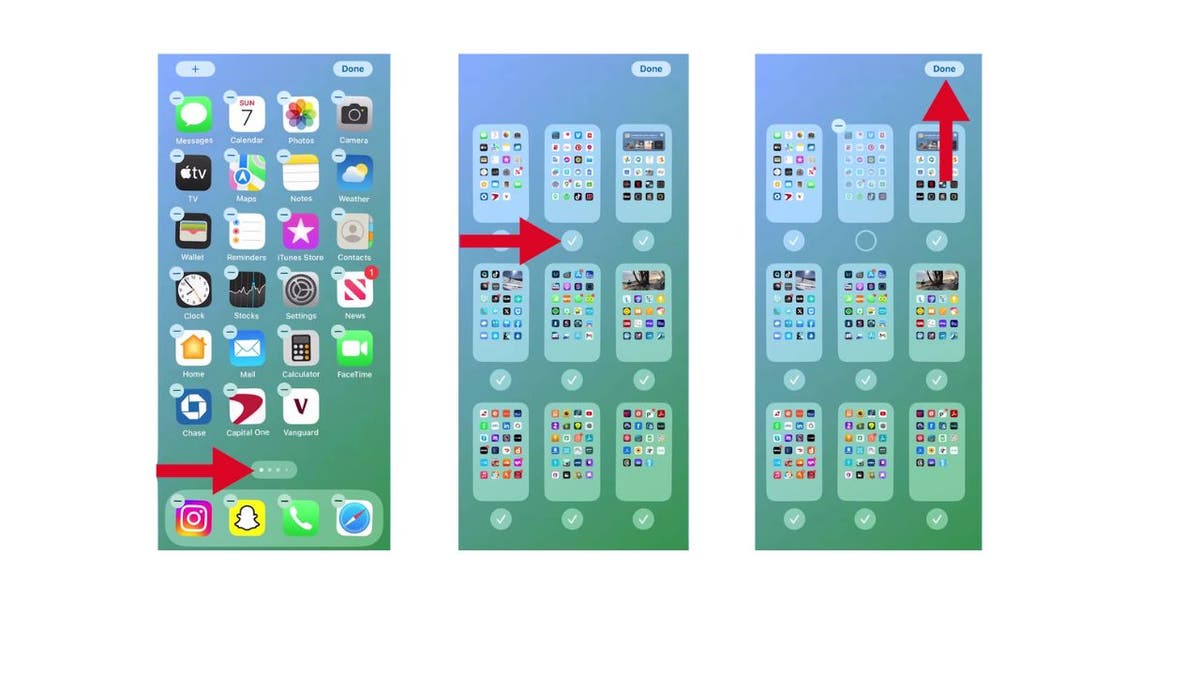
Steps to hide a whole page of apps on your iPhone (Kurt “CyberGuy” Knutsson)
Your selected page of apps is now out of sight, creating a cleaner and more organized home screen.
How to hide an app from search on iPhone
Hiding an app on your iPhone prevents it from showing up on the home screen, but it will still be discoverable through search. If you want to avoid that, you can also hide an app from search on your iPhone:
- Open Settings
- Tap Siri & Search
- Scroll down to locate the app you want to hide and tap it.
- Click Siri & Search again
- Tap Show App in Search
- When the toggle appears gray, that means the app is hidden from search.
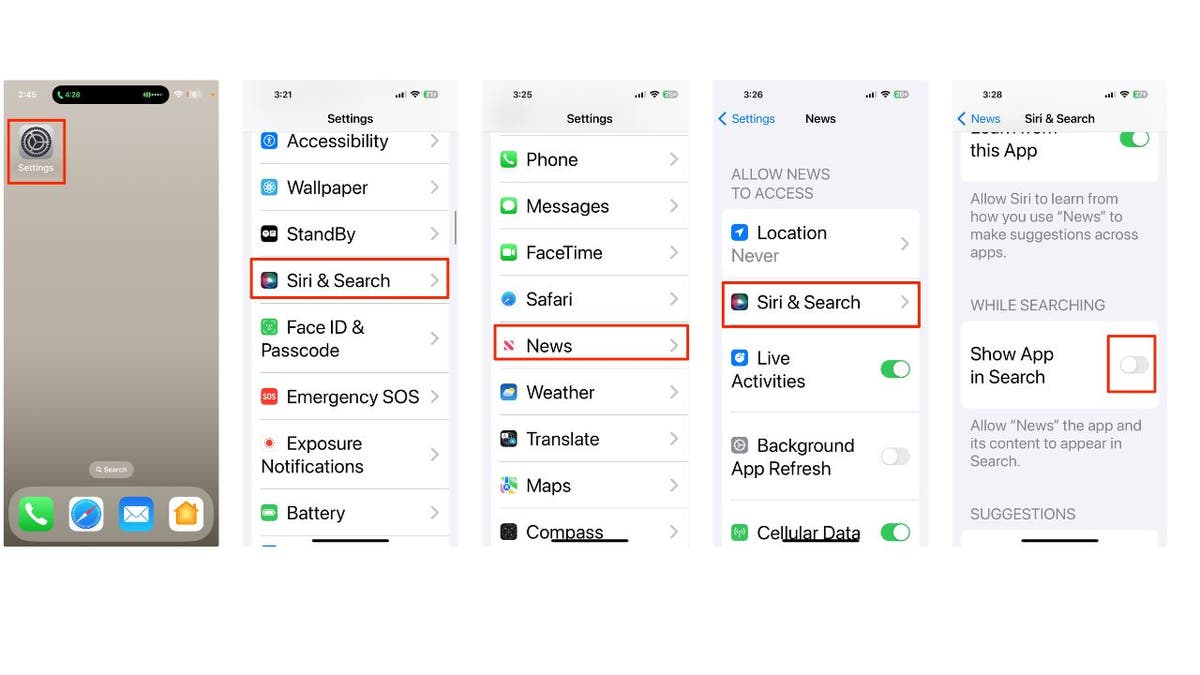
Steps to hide an app from search on iPhone (Kurt “CyberGuy” Knutsson)
MORE: HOW TO UPDATE YOUR PASSCODE ON YOUR IPHONE
Bringing the app or page of apps back
Change your mind? No problem. Here’s how to bring back your hidden apps:
How to bring back a single app
- Locate the app in the App Library
- Long press on the app and drag it back to your home screen.
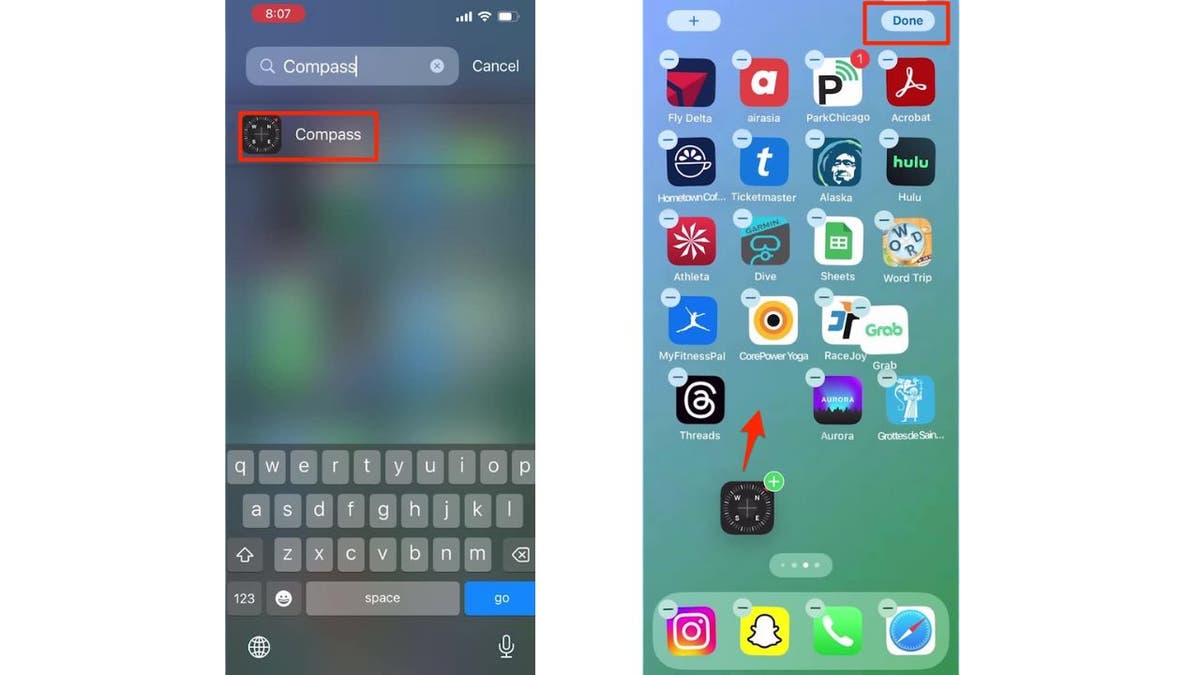
How to bring an app back on iPhone (Kurt “CyberGuy” Knutsson)
How to bring back a page of apps
- Long-press an empty area on your home screen
- Tap the dots at the bottom of the home screen
- Then, select the previously hidden page by tapping the empty bubble.
- Finish by tapping Done
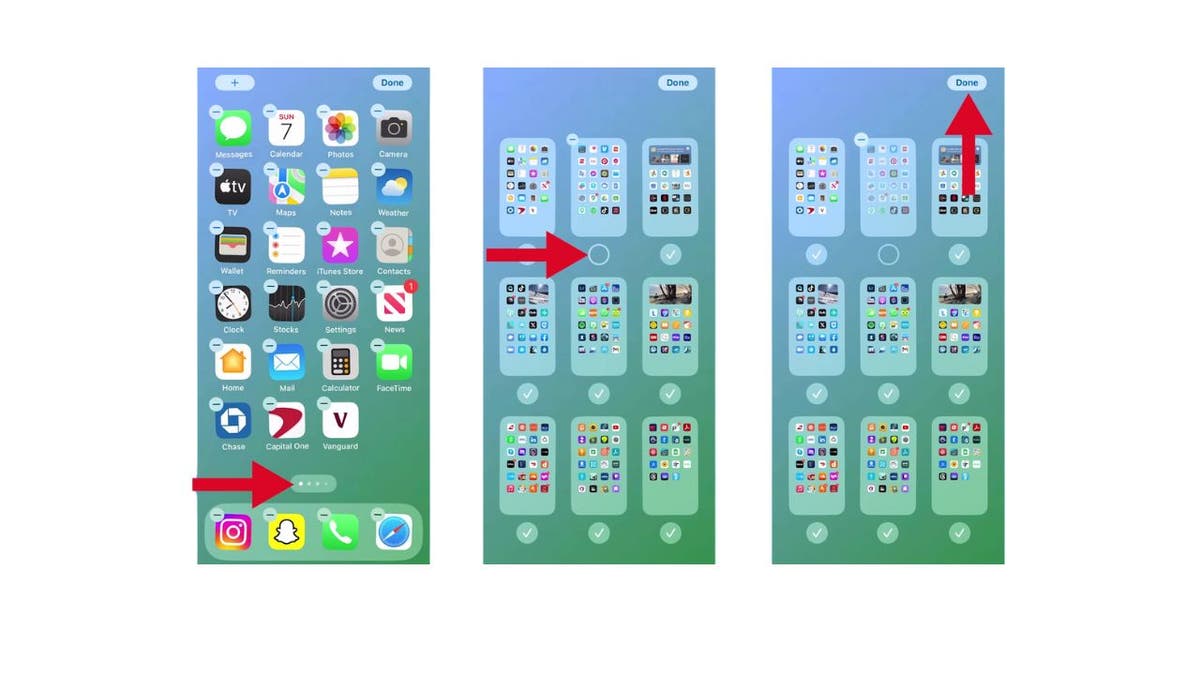
Steps to bring back a page of apps on iPhone (Kurt “CyberGuy” Knutsson)
MORE: 8 WAYS TO LOCK UP YOUR IPHONE’S PRIVATE STUFF
Kurt’s key takeaways
Customizing your iPhone’s app visibility is about privacy and personalizing your user experience. Whether you’re hiding a single app or an entire page, the process is reversible, giving you the flexibility to change things up as needed. Remember, your apps are just out of sight, ready to be summoned back whenever you choose.
In what situations do you find it most necessary to conceal apps or pages on your iPhone? Let us know by writing us at Cyberguy.com/Contact.
For more of my tech tips & security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you’d like us to cover.
Answers to the most asked CyberGuy questions:
Copyright 2024 CyberGuy.com. All rights reserved.