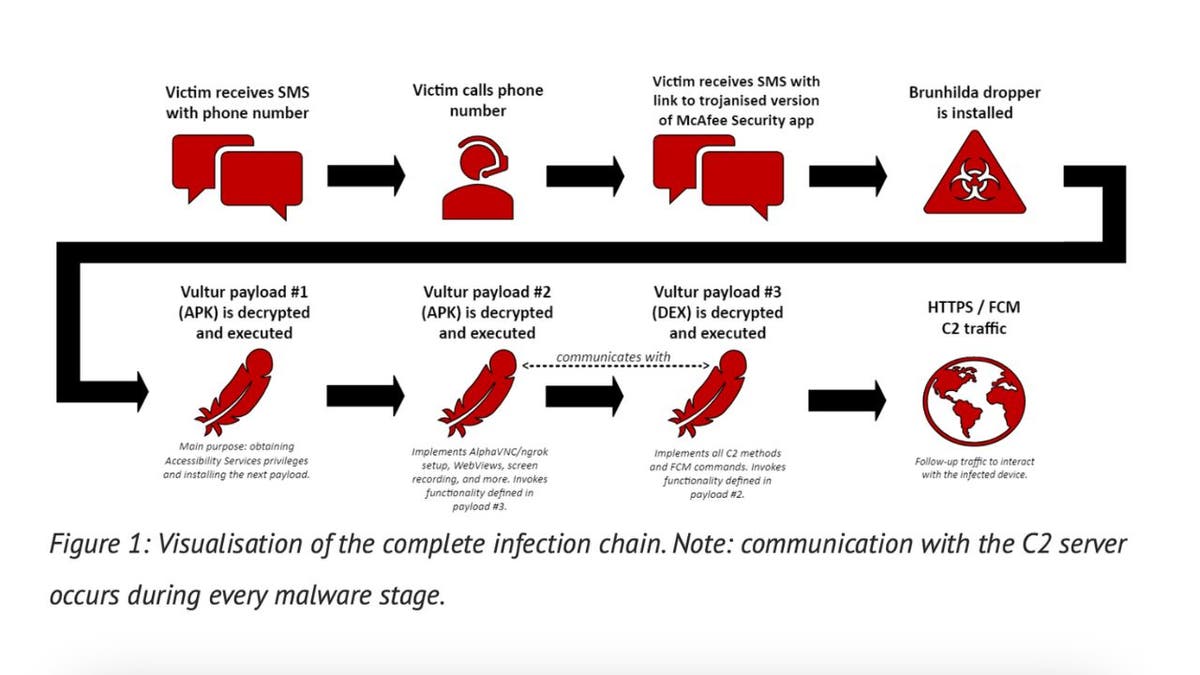
Researchers at MIT’s Computer Science and Artificial Intelligence Laboratory (CSAIL) recently revealed a startling new privacy threat.
Our smartphones’ ambient light sensors might be turned into makeshift cameras.
A woman on her iPhone (Kurt “CyberGuy” Knutsson)
From brightness adjustment to privacy invasion
Ambient light sensors are commonplace in smartphones, primarily used to adjust screen brightness according to environmental lighting. However, CSAIL researchers have demonstrated that these sensors could potentially be repurposed to capture images of a user’s surroundings.
By employing a computational imaging algorithm, they managed to recover environmental images from the perspective of the phone’s screen, utilizing only the light intensity data from these sensors.
CLICK TO GET KURT’S FREE CYBERGUY NEWSLETTER WITH SECURITY ALERTS, QUICK VIDEO TIPS, TECH REVIEWS AND EASY HOW-TO’S TO MAKE YOU SMARTER
Two people looking at their iPhones (Kurt “CyberGuy” Knutsson)
A comprehensive privacy threat
The implications of this discovery are far-reaching.
“Ambient light sensors are tiny devices deployed in almost all portable devices and screens that surround us in our daily lives,” notes Princeton University professor Felix Heide. The study underscores a privacy threat that spans a broad spectrum of devices, previously underestimated in its potential impact.
WHAT IS ARTIFICIAL INTELLIGENCE (AI)?
A person on a cell phone (Kurt “CyberGuy” Knutsson)
Gesture interception and interaction capture
Beyond static images, the study suggests that ambient light sensors could intercept user gestures, like swiping and sliding, capturing interactions with phones during activities such as video watching. This capability challenges the belief that ambient light sensors are harmless in terms of private data exposure.
An iPhone (Kurt “CyberGuy” Knutsson)
MORE: BEST WAY TO PROTECT YOUR DEVICES FROM GETTING HACKED
The call for tighter permissions
Yang Liu, a Ph.D. candidate at MIT EECS and CSAIL, warns that ambient light sensors, in conjunction with display screens, can capture our actions without consent, posing significant privacy risks. The researchers urge operating system developers to tighten permissions for these sensors, reducing their precision and sampling rate.
Person on an iPhone (Kurt “CyberGuy” Knutsson)
Looking ahead: Designing for privacy
To mitigate these security concerns, the study proposes granting users control over ambient light sensor permissions akin to camera permissions. Additionally, future device designs might include ambient light sensors positioned away from the user, such as on the side of the device, to prevent unauthorized visual data capture.
While the study’s findings prompt a reevaluation of sensor permissions and design, it’s equally important to recognize the broader context of smartphone security vulnerabilities. Let’s delve into the realm of spyware, another pressing concern where even the most vigilant users can find themselves compromised.
A woman talking on her cell phone (Kurt “CyberGuy” Knutsson)
Understanding spyware vulnerability on your smartphone
You might not realize it, but your phone could be more exposed to spyware than you think. Just a small slip-up while you’re browsing the web, and you could accidentally invite a cyber-spy into your life. If you’re an Android user, be extra cautious. Your phone is usually more at risk than iPhones.
But here’s the kicker. Even if you’re super careful, you’re not totally out of the woods. If you don’t update your phone’s software regularly or if you’ve jailbroken it, you’re playing with fire. Here are some telltale signs of spyware on your phone.
A woman on her smartphone (Kurt “CyberGuy” Knutsson))
MORE: SNEAKY SPYWARE IS AFTER YOUR MOST SENSITIVE DATA
The telltale sign of spyware on your phone
Is your phone acting strange? Here are the telltale signs of spyware on your device.
Unusual noises: Beeping, faint voices or static during calls might not just be network issues. They could signal an eavesdropping attempt.
Performance lags: If your phone suddenly slows down or the battery drains rapidly, spyware might be hogging your resources.
Sensors activate unexpectedly: Modern smartphones signal when cameras and mics are in use. If this happens sans your input, investigate promptly.
Mysterious apps and files: New, unrecognizable apps or files might indicate that your phone’s security has been breached.
Excessive pop-ups and spam: An uptick in ads, error messages or scam texts may be adware, a common companion to spyware.
Overheating issues: Like performance lags, overheating can suggest that spyware is overworking your phone’s internals.
Smartphone on the seat of a vehicle (Kurt “CyberGuy” Knutsson)
MORE: MALICIOUS ANDROID SPYWARE DETECTED IN OVER 100 POPULAR APPS
Several steps you can take to protect yourself from spyware on your smartphone
1. Have good antivirus software: Yes, antivirus protection can help detect and disable spyware on your smartphone. The best way to protect yourself from clicking malicious links that install malware that may get access to your private information is to have antivirus protection installed on all your devices. This can also alert you of any phishing emails or ransomware scams. Get my picks for the best 2024 antivirus protection winners for your Windows, Mac, Android & iOS devices.
2. Remove unfamiliar apps and files: If you suspect your phone has been hacked, promptly remove any unfamiliar apps.
3. Restart your device: Rebooting your phone can sometimes stop spyware from running.
4. Update to the latest software: As mentioned before, updates can patch vulnerabilities.
5. Be cautious when browsing: Avoid clicking on suspicious links or downloading files from untrusted sources.
6. Update your phone regularly: Updates often include security patches that can help protect your device from spyware and other vulnerabilities.
7. Don’t jailbreak your phone: Jailbreaking removes security restrictions that can make your phone more susceptible to spyware.
8. Look for unusual activity: This includes unusual noises during calls, performance lags, unexpected sensor activation, mysterious apps or files, excessive pop-ups and overheating.
9. Delete unwanted or unused apps: Some apps use your device’s camera and microphone and collect your data even while it is not in use. Getting rid of unused apps frees up storage space on your phone and declutters your lock screen. It can also eliminate one more potential app that might be collecting information from you unknowingly.
On an iPhone:
- Hard press the app icon of the app you want to delete
- Select Remove App
- You’ll be prompted to confirm your decision in the next window by tapping Delete App
- Then again by tapping Delete
On an Android:
- Go to the Google Play Store app
- At the top right, tap the Profile icon
- Select Manage apps & devices, click Manage
- Select name of the app you want to delete
- Select Uninstall
Android settings may vary based on the manufacturer’s settings.
GET FOX BUSINESS ON THE GO BY CLICKING HERE
While it may seem like an extra effort to review and change your apps’ permission settings, it’ll give you more peace of mind knowing which apps have access to specific device functions and data. Most devices now have a dedicated part of their settings to view which apps are using the different functions of your phone and what data it has access to.
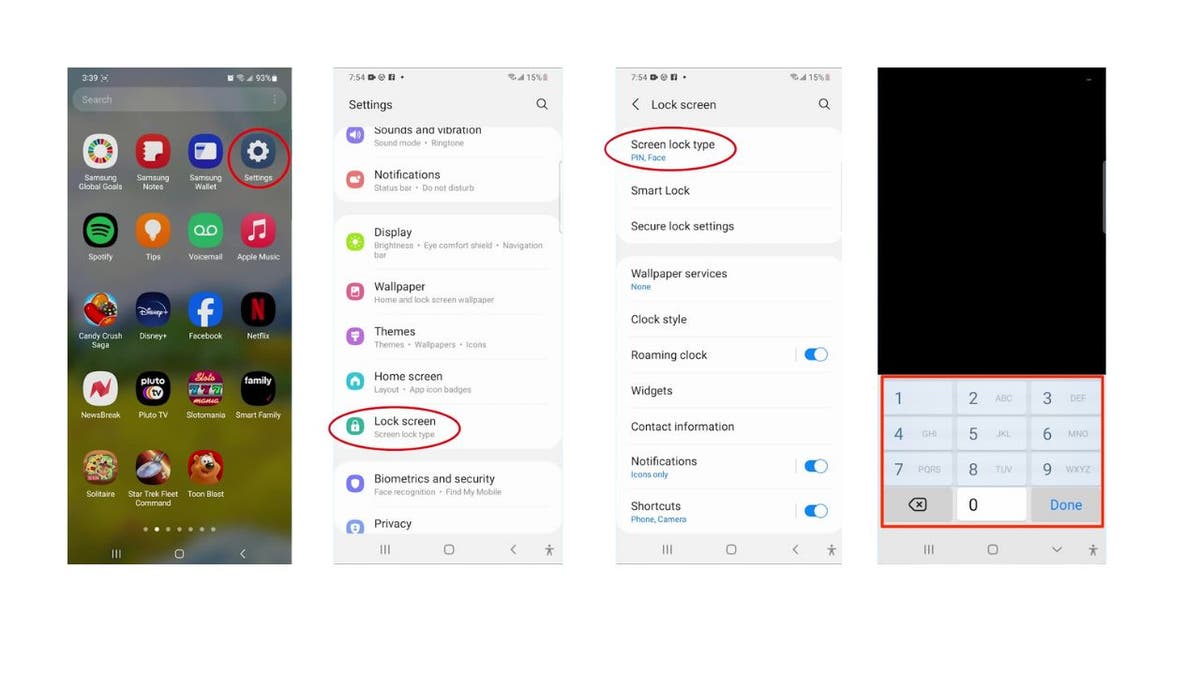
10. Changing camera settings: It may seem simple to just give access to your camera to certain apps. This way, you can easily use the camera function whenever you pull up the app to use. There are, however, apps that do not need access to your camera to function. Does your navigation app need access to your camera even when it is not in use? Take back control of your camera by using the steps below to find out which apps have access to your camera and turn it on or off.
On an iPhone:
- Go to Settings
- Scroll down and select Privacy or Privacy & Security
- Select Camera
- You can see which apps have access to your camera. Of course, you can leave the apps where it makes sense to have access to your camera toggle on. For apps that do not, you can toggle access off (it will be grayed out)
On an Android:
Android settings may vary based on the manufacturer’s settings.
- Open Settings
- Select Apps
- Select the app you want to change (If you can’t find it, select ‘See all apps’)
- Select Permissions to view if you allowed or denied any permissions for the app
- To change a permission setting, select it, then choose Allow only while using the app, Ask everytime or Don’t allow
11. Restrict camera and microphone permissions: Restricting camera and microphone permissions can make it more difficult for spyware to access these features.
On an iPhone:
- Go to Settings
- Scroll down and select Privacy or Privacy & Security
- Select Microphone
- You can see which apps have access to your microphone. Of course, you can leave the apps where it makes sense to have access to your microphone toggle on. For apps that do not, you can toggle access off (it will be grayed out)
On an Android:
Android settings may vary based on the manufacturer’s settings.
- Open Settings
- Select Apps
- Select the app you want to change (If you can’t find it, select ‘See all apps’)
- Select Permissions to view if you allowed or denied any permissions for the app
- To change a permission setting, select it, then choose Allow only while using the app, Ask everytime or Don’t allow
MORE: NEWLY IPHONE SPYWARE TOOL SOLD TO GOVERNMENTS FOR TARGETED SURVEILLANCE
Kurt’s key takeaways
In a world where our smartphones are virtual extensions of ourselves, the discoveries at MIT’s CSAIL cast a new light on what we often take for granted. As we navigate the delicate balance between convenience and privacy, it’s clear that the devices we depend on daily harbor capabilities far beyond their intended use, prompting a necessary conversation on security, awareness and the evolving landscape of digital privacy.
CLICK HERE TO GET THE FOX NEWS APP
With the revelation that devices we use daily, like smartphones, can be exploited in ways that compromise our privacy — such as converting ambient light sensors into makeshift cameras — what steps do you believe technology companies and governments should take to protect personal privacy? Let us know by writing us at Cyberguy.com/Contact
For more of my tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter
Ask Kurt a question or let us know what stories you’d like us to cover
Answers to the most asked CyberGuy questions:
Copyright 2024 CyberGuy.com. All rights reserved.
Kurt “CyberGuy” Knutsson is an award-winning tech journalist who has a deep love of technology, gear and gadgets that make life better with his contributions for Fox News & FOX Business beginning mornings on “FOX & Friends.” Got a tech question? Get Kurt’s free CyberGuy Newsletter, share your voice, a story idea or comment at CyberGuy.com.